Aug 18, 2021--Written by Divine Sufor Anye, Phd. The world has never been as connected or as digital as it is today. From personal devices to complicated industrial systems, digitization is now all around us. Wherever you look, the world seems to be taking on a digital dimension. But where does Africa stand in this... Read more
Category: Digital Transformation
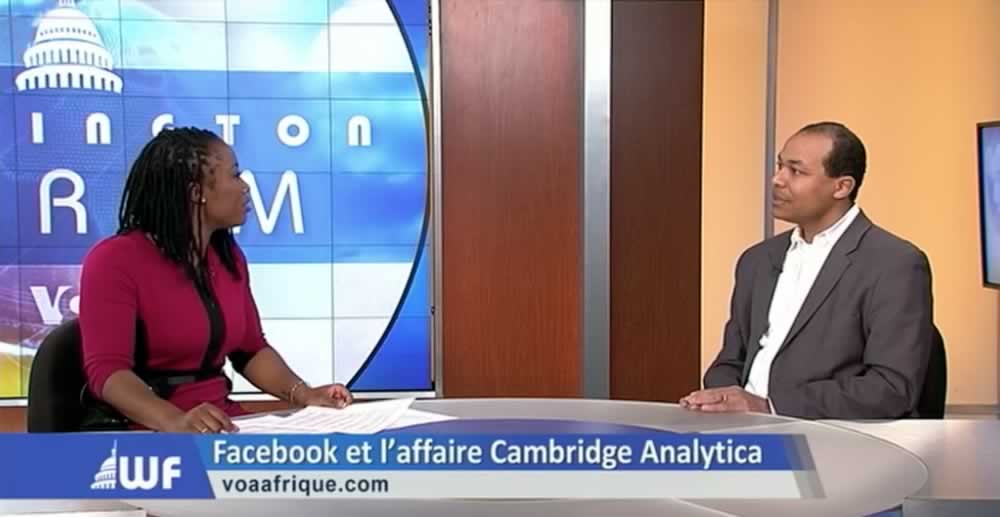
Washington Forum March 30, 2018: Should Africa be wary of Facebook?
Apr 3, 2018, Washington, DC--Frank Welffens, Managing Partner at USAFCG, joined the Washington Forum at Voice of America in Washington, DC, and participated in the discussion on information security and Facebook in light of Cambridge Analytica’s scandal. Source: https://www.voaafrique.com/a/4323744.html Discussion Topic: Panic winds at Facebook, following the revelations of data use of millions of users... Read more
Cybersecurity in the Age of Digital Transformation
Jan 10, 2018--As companies embrace technologies such as the Internet of Things, big data, cloud, and mobility, security must be more than an afterthought. But in the digital era, the focus needs to shift from securing network perimeters to safeguarding data spread across systems, devices, and the cloud. by MIT Technology Review Custom January 23, 2017... Read more
Global Cybersecurity Index 2017
Jul 20, 2017--The Global Cybersecurity Index (GCI) is a survey that measures the commitment of Member States to cybersecurity in order to raise awareness. The second edition of the Global Cybersecurity Index 2017, released by the International Telecommunications Union (ITU), an agency of the United Nations, measured the commitment of ITU Member States to cybersecurity and... Read more
African Union Cybersecurity Profile: Seeking a Common Continental Policy
Sep 23, 2016--Africa is now home to some of the world’s fastest growing economies–the terms “Africa rising” and “lions on the move” have both been used in recent years to capture the positive economic outlook for the continent. In tandem with this new economic boom, countries in the African Union (AU) have experienced explosive growth... Read more